The recently published Verizon 2023 Data Breach Investigations Report provides insights into the tactics, techniques, and procedures that cyber actors are using to gain access to networks to achieve their objectives. The data for the report comes from security incidents and data breaches between Nov. 1, 2021, to Oct. 31, 2022, which this year includes 953,894 security incidents and 254,968 confirmed breaches, including more than 16,000 security incidents and 5,200 that were investigated by Verizon.
This year, 74% of all data breaches involved the human element, down from 82% of data breaches in 2022. 83% of data breaches involved external actors, the vast majority of which (95%) were financially motivated cyberattacks. The most common ways that threat actors gained access to networks were the use of stolen credentials, phishing, and the exploitation of vulnerabilities.
The report reveals business email compromise (BEC) attacks have doubled from the previous year, and now account for more than half of all social engineering attacks. As well as increasing in number, these attacks have grown in sophistication. These were part of an increase in pretexting incidents, where attackers trick people into giving up information. Pretexting incidents have been growing rapidly in recent years, from pre-2019 levels of less than 1% of all incidents to close to 4% of incidents in 2023. Phishing accounts for 44% of all social engineering incidents and it was the most common form of social engineering for years but has now been overtaken by BEC attacks. The median amount stolen in BEC attacks is $50,000.
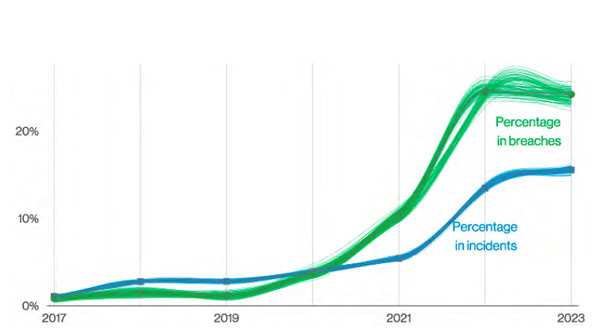
Ransomware continues to be extensively used in cyberattacks, and while ransomware was used in high numbers of attacks, these attacks appear to be leveling off. That said, the number of ransomware attacks in the past two years is higher than the number of attacks in the previous five years combined. In 2023, ransomware was used in 24% of data breaches and 15.5% of all security incidents and was used in 62% of attacks conducted by organized crime groups and 59% of financially motivated attacks. Ransomware actors most commonly gained access to victims’ networks through email, desktop sharing software, and web applications, with only 5% of attacks involving the exploitation of software vulnerabilities.
While the median payment to ransomware gangs has decreased – which based on limited available data fell from around $20,000 in 2022 to $10,000 in 2023 – Verizon suggests that there appears to have been an increase in attacks on smaller companies, where the ransoms that can be obtained are significantly lower. That said, the cost of remediating ransomware attacks continues to increase.
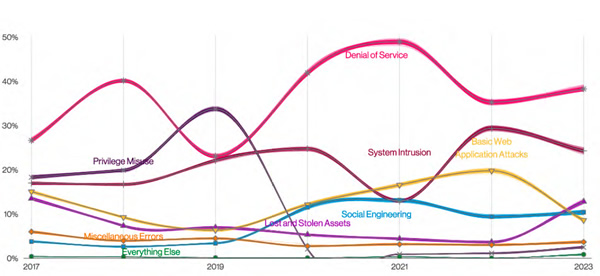
Denial of Service (DoS), including Distributed Denial of Service (DDoS), was the most prevalent attack action, followed by system intrusions, basic web application attacks, lost and stolen assets, and social engineering. Over the past two years, there have been increasingly larger DDoS attacks, and Verizon notes that there has been a notable increase in DDoS attacks termed DNS water torture. These attacks are conducted on shared DNS infrastructure and involve querying random name prefixes on the DNS cache server, so it always misses and forwards it to the authoritative server.
The most cited exploited vulnerability was, unsurprisingly, the Log4J vulnerability CVE-2021- 44228. While the specific vulnerability that was exploited in attacks was not always provided (only 20.6% of such events named the vulnerability), out of those where a vulnerability was named, 90% named CVE-2021- 44228. Web application attacks accounted for 25% of data breaches and were largely aimed at leveraging stolen credentials and exploiting vulnerabilities to gain access to victims’ assets. 86% of web application attacks involved the use of stolen credentials.
The 89-page report can be viewed/downloaded here.

